Wicket is committed to the responsible use and application of facial authentication technology, and to that end, takes security and privacy very seriously. Learn more about how we design our technology for that commitment below.




Wicket algorithms are developed and optimized in-house by our team of scientists in Cambridge, MA, and are designed to address bias. We submitted to NIST testing, viewed as the industry gold standard. The results show Wicket has a 99.7% accuracy rate across all demographic categories and is top 3 for accuracy of matched decisions in the U.S. at the time of submission.
Wicket products require that different data and images be captured and held for varying time frames, depending on the customer’s use case. Data is only stored for the purpose of the product and is automatically purged according to the data policies of Wicket customers for the intended use of that data.
Images of the faces of individuals that present themselves to an Access touch-point are captured and retained for logging purposes. This data is purged from the system according to the specified data configuration of the customer.
All users must actively opt in, and users who wish to opt out of the program may do so immediately and at any time.
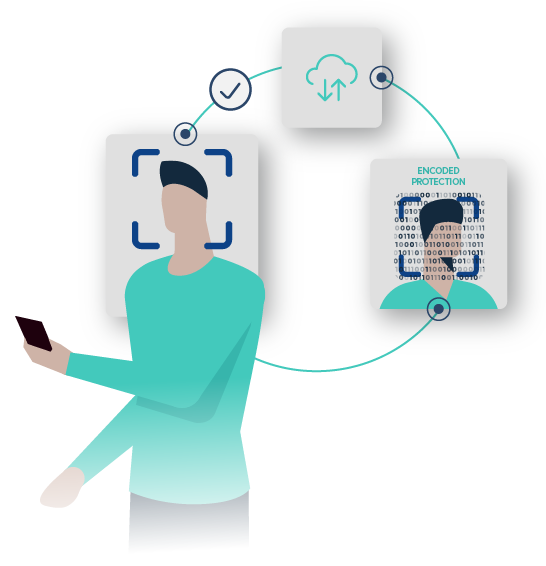
Customers exclusively own the database where information lives, and all Personally Identifiable Information (PII) lives on the cloud, preventing 3rd party access or sharing.
We use mathematical representations of faces instead of actual photos, meaning devices store no photos and keep your identity safe, even when compromised.
While Wicket’s computer vision algorithms could technically be classified as a facial recognition system, we prefer to use the term Facial Authentication.
Facial recognition systems like those used by law enforcement or security agencies (to identify an unknown individual by running an image through an extensive database) are based on a surveillance model.
Wicket differs from this approach in two ways:
Firstly, Wicket has an opt-in-only model. We do not use our technology to keep people out, but rather to let known faces (registered users) in—only people who have explicitly opted into Wicket-powered services can use them.
Secondly, Wicket’s Facial Authentication system is designed to protect the privacy of those who do not want to be captured at all. To ensure unwilling participants aren’t scanned by Wicket, users must physically present to a Wicket sensor to gain access to confirm that the user is: